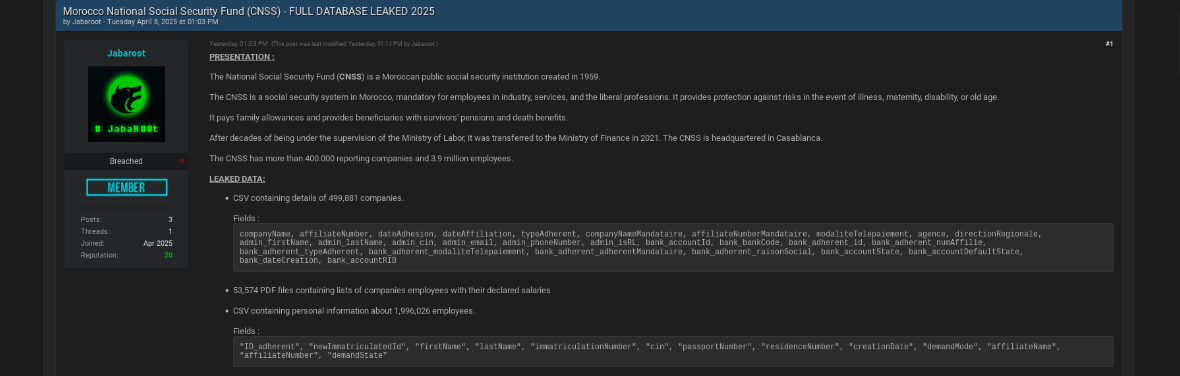
April 8, 2025. Actor “Jabaroot” dumps Morocco’s entire National Social Security Fund (CNSS) database. No ransom, just a straight 549MB archive containing the financial DNA of an entire nation.
The package:
- 53,000+ individual PDF payslips with full salary breakdowns
- 2 massive CSV exports covering ~500,000 companies and ~2,000,000 employees
- Records fresh from November 2024 - we’re talking current operational data
- Complete PII exposure: social security numbers, bank RIBs, exact salaries, personal contact details, employment histories
We’re looking at the complete financial infrastructure of Morocco laid bare. Royal Air Maroc employees, Attijariwafa Bank staff, workers from Siger (the King’s personal holding company), even members of the royal household all their financial details sitting in a password-protected archive with the password “jabaroot”.
The actor posted it straight to BreachForums and Telegram under the headline “Morocco National Social Security Fund (CNSS) FULL DATABASE LEAKED 2025.” No demands, no negotiations. This is economic warfare with a hacktivist mask.
Authenticity Verification
First question with any leak this size: is it real or fabricated garbage? After pulling apart the archive, this is definitely the real deal.
Archive Breakdown:
- File:
CNSS - Moroccan National Social Security Fund.7z - Size: 575,692,336 bytes (549MB compressed)
- Password:
jabaroot - Compression: LZMA2:31 with 7zAES encryption
- Contents: 2 CSV files + directory containing 53,000+ PDFs
Validation:
Every PDF in this dump was generated between November 19-23, 2024, during Moroccan business hours (CET timezone). The metadata is consistent across all files:
$ exiftool dump/**/*.pdf | grep -Ei 'Creator|Producer|Create Date'
Creator: JasperReports Library version 6.6.0
Producer: iText 2.1.7 by 1T3XT
Create Date: 2024:11:23 22:35:23+01:00
Modify Date: 2024:11:23 22:35:23+01:00
JasperReports 6.6.0 and iText 2.1.7 older Java reporting tools still common in government finance. The timestamps span four days, hinting at automated batch exports from an internal reporting setup.
Hash Analysis:
$ find dump -type f -exec shasum -a 256 {} \; > hashes.txt
$ cat hashes.txt | uniq -d
# [no output - every file is unique]
Zero duplicate hashes across 53,000+ files. Each PDF was individually rendered with unique data - impossible to fake at this scale. This confirms access to the actual generation layer, not just static file exports.
File Naming Pattern: PDFs follow sequential numeric naming from 67.pdf up to 160021766.pdf. No randomness, no gaps in the sequence classic database auto increment behavior. The CSV files contain matching record IDs that correlate perfectly with the PDF filenames.
Archive Metadata:
$ 7zz l 'CNSS - Moroccan National Social Security Fund.7z' | head -15
Date Time Attr Size Compressed Name
2024-11-30 00:00:05 D.... 0 0 ATTESTATIONS SALARIES DECLARES
2025-04-08 10:45:52 ....A 337544633 575112208 ADHERENTS.csv
2024-11-22 19:33:06 ....A 108747 ATTESTATIONS SALARIES DECLARES/100000.pdf
The CSV export timestamp (April 8, 2025 10:45:52) matches exactly when Jabaroot posted the leak. Someone exported this data specifically for the dump, then packaged it immediately for release.
This isn’t scraped web data or reconstructed information. This is a direct export from CNSS’s internal database and reporting infrastructure.
Data Structure: The leak contains two primary datasets with complete financial and personal information:
ADHERENTS.csv (337MB, ~2M records): Each employee record contains:
- CNSS identification number (unique social security ID)
- National ID (CIN) and passport/residence permit numbers
- Full name, date of birth, nationality
- Complete employment history with employer CNSS IDs
- Subscription dates, affiliation status, regional office assignments
- Contact information: personal email, phone numbers
- Salary attestation dates and net payment amounts
- Application modes and processing status
SALARIES.csv (Company records, ~500k entries): Each company record exposes:
- CNSS registration and affiliate identification numbers
- Complete administrative contact details: names, national IDs, emails, phone numbers
- Full banking information: RIB details, account creation dates, bank codes, account status
- Subscription and adhesion dates, payment processing modes
- Regional office assignments and processing history
- Corporate structure and affiliation data
PDF Payslips (53,000+ individual files): Each PDF contains a complete salary breakdown:
- Employee personal details matching CSV records
- Employer information and CNSS registration
- Detailed salary components: base pay, bonuses, deductions, net amount
- Social security contributions and tax withholdings
- Pay period dates and issuance timestamps
- Official CNSS formatting and digital signatures
The data structure reveals this came from a Java-based reporting system (JasperReports) with direct database access. Field names, data types, and relational structure all point to internal CNSS taxonomy not external scraping or third-party integration.
Threat Actor: “Jabaroot”
Operational Tradecraft
The attack methodology shows competent but not sophisticated tradecraft. Just opportunistic exploitation of weak security controls.
Initial Access Vector: The data volume and export format strongly suggest legitimate credential access or exploitation of an unpatched internal server. The ability to generate 53,000+ individual PDFs through JasperReports indicates access to the actual reporting infrastructure, not just database dumps.
Looking at the timeline:
- November 19-23, 2024: Batch PDF generation during business hours
- April 4-8, 2025: Teaser content posted to build credibility
- April 8, 2025 10:45:52: Final CSV export timestamp
- April 8, 2025: Full archive release
This 4-month gap between data generation and release suggests:
- Compromise of backup/archive systems containing November data
Collection and Staging: The actor had access to multiple CNSS systems:
- Database layer: Direct CSV exports with complete record sets
- Reporting layer: JasperReports infrastructure for PDF generation
- File system: Ability to package and compress 549MB of data
The sequential PDF naming (67.pdf to 160021766.pdf) and perfect correlation with CSV record IDs indicates systematic, automated collection not manual cherry-picking.
Exfiltration and Distribution: Multi-stage release strategy designed for maximum impact:
- Initial Hosting: Archive uploaded to BiteBlob file-sharing service
- Credibility Building: Posted teaser screenshots on BreachForums
- Primary Distribution: Telegram channel “JabarootDZ” with 9,000+ subscribers
- Amplification: Cross-posted to multiple underground forums and channels
OpSec Assessment:
The OpSec profile suggests an hacktivist rather than state-sponsored operator competent enough to avoid immediate attribution but not sophisticated enough to eliminate all traces.
Attribution Analysis
The geopolitical messaging throughout this campaign points clearly toward Algerian-aligned actors, but the technical indicators tell a more complex story.
Primary Persona: “Jabaroot”
- Telegram channel: @JabarootDZ (now deleted)
- Archive password: “jabaroot”
- The name comes from the Arabic root ج-ب-ر (J-B-R), like “Al-Jabbar” The Compeller.
- Channel accumulated 9,400+ views before deletion
Secondary Alias: “3N16M4”
- Briefly forwarded content to Jabaroot channel before being scrubbed
- Online footprint traces to possible identity “Rachid Mz.” (unconfirmed)
- Technical background suggested by alias structure and operational choices
- Infrastructure geolocation traces to Germany
Geopolitical Messaging:
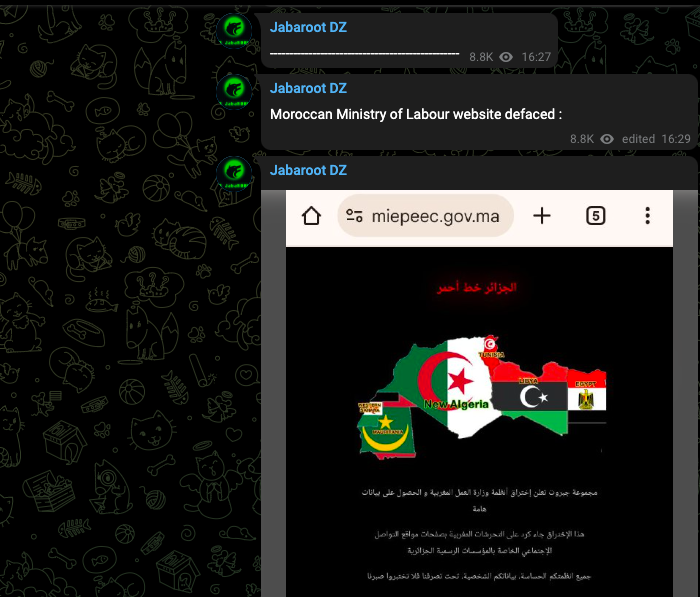
The now-deleted Telegram post (hxxps[://]t[.]me/JabarootDZ/42) contained explicit political framing:
الجزائر خط أحمر
Algeria is a red line
مجموعة جبروت تعلن اختراق أنظمة وزارة العمل المغربية والحصول على بيانات هامة.
Jabaroot Group announces the breach of Moroccan Ministry of Labor systems and the acquisition of sensitive data.
هذا الإختراق جاء كرد على التحرشات المغربية بصفحات مواقع التواصل الإجتماعي الخاصة بالمؤسسات الرسمية الجزائرية.
This breach comes as a response to Moroccan harassment campaigns on social media targeting official Algerian institutions
Website Defacements: The actor also defaced miepeec.gov.ma (a Ministry-affiliated site) with the same “الجزائر خط أحمر” message at 16:29. Although not directly linked to CNSS, this shows wider reconnaissance and access within the gov.ma infrastructure.
Operational Timeline:
- Early April 2025: Moroccan-aligned groups targeted Tunisian entities with basic DDoS attacks
- April 4-8, 2025: Jabaroot teaser campaign builds momentum
- April 8, 2025: Full CNSS archive release with explicit anti-Morocco messaging
Indicators:
- Telegram location metadata: Tunisia
- Infrastructure traces: Germany (unconfirmed)
- Linguistic patterns: Algerian Arabic dialect in messaging
- No profit motive: purely ideological/political intent
Assessment:
This appears to be a multi-national North African hacktivist operation with the following likely structure:
- Tunisian operator: Gained initial access to CNSS systems (supported by 3N16M4 traces)
- Algerian amplification: ”Jabaroot” persona handled political messaging and distribution
The pattern fits classic regional proxy warfare: actors aligned with state interests yet acting independently. The four-month gap between data collection (November 2024) and release (April 2025) hints at coordination amid rising geopolitical tensions.
Attribution Confidence: Medium-High for Algerian alignment, Medium for specific actor identification. The geopolitical messaging, linguistic patterns, and target selection strongly indicate Algerian-sponsored or aligned activity, but technical attribution to specific individuals remains speculative based on available OSINT.
The Broader Attack Surface: Gov.ma Infrastructure
The CNSS breach is just one piece of a bigger picture a sign of deep security gaps across Morocco’s entire gov.ma network. The same actor showed access to multiple government sites, exposing a broad and persistent vulnerability.
Case Study: miepeec.gov.ma Compromise
During the same timeframe as the CNSS leak, Jabaroot defaced miepeec.gov.ma (Ministry of Equipment and Water-affiliated site) with their signature “الجزائر خط أحمر” message. But the defacement was just the visible tip of a much deeper compromise.
Timeline Analysis:
- Pre-April 4, 2025: Site operating normally
- April 4-8, 2025: Front-end replaced with “suspended” banner
- Post-April 8: Backend directories remained accessible despite suspension
Assessment: Even after the front-end takedown, directory paths like /wp-content/Upload remained browsable. Live reconnaissance revealed:
# Example of exposed directory structure
/wp-content/uploads/2019/
/wp-content/uploads/2020/
/wp-content/uploads/2021/
# ... continuing through 2024
Sensitive documents dating back to 2019 were still downloadable without authentication:
- Internal ministry communications
- Contract details with private companies
- Personal email addresses of government officials
- Financial agreements and procurement documents
Security Failures Identified:
- WordPress CMS with directory indexing enabled
- No access controls on uploaded content
- Backend systems accessible despite front-end suspension
- Zero lifecycle governance for archived documents
Systemic Infrastructure Problems This pattern repeats across dozens of gov.ma domains. Basic reconnaissance reveals:
Common Vulnerabilities:
- Unpatched WordPress installations (many running versions 3+ years old)
- Default admin credentials on development/staging sites
- Exposed .git directories containing source code and credentials
- Publicly accessible database backups and configuration files
- Directory traversal/SQL vulnerabilities allowing file system access
Operational Security Gaps:
- No centralized security monitoring across gov.ma infrastructure
- Inconsistent patching and update procedures
- Development and production environments sharing credentials
- Lack of incident response procedures
- No security awareness training for government web administrators
The Reconnaissance Goldmine
For an attacker like Jabaroot, this infrastructure represents a target-rich environment where sophisticated techniques aren’t necessary. Basic automated scanning tools can identify:
- Vulnerable WordPress plugins across multiple government sites
- Exposed administrative interfaces with weak authentication
- Publicly accessible internal documents and communications
- Cross-site credential reuse enabling lateral movement
- Unmonitored file upload capabilities for persistence
The miepeec.gov.ma compromise demonstrates that Jabaroot didn’t need skills to access CNSS - they just needed patience and awareness of where no one was watching. When dozens of government domains exhibit the same security hygiene failures, attackers don’t need to target specific systems. The targets present themselves.
Infrastructure Assessment:
The gov.ma ecosystem suffers from:
- Legacy System Dependencies: Critical infrastructure running on outdated, unpatched systems
- Decentralized Security: No unified security standards or monitoring across government domains
- Poor Change Management: Updates and patches applied inconsistently or not at all
- Inadequate Access Controls: Overprivileged accounts and shared credentials
- No Security Lifecycle: Systems deployed without security review and never reassessed
This creates an environment where a single compromised credential or unpatched vulnerability can provide access to multiple government systems, explaining how Jabaroot could move from website defacements to complete database exfiltration.
Impact Assessment
This leak enables multiple attack vectors:
Financial Fraud: Real SSNs + exact salaries + bank details = high-success phishing campaigns. Scammers can reference actual pay dates, amounts, and departmental codes.
Identity Theft: Complete PII packages for 2M+ individuals. Perfect for synthetic identity schemes.
Economic Manipulation: Selective data releases targeting specific sectors (banking, aviation, logistics) to influence markets or create operational chaos.
Political Warfare: Gradual leaking of high-ranking officials’ payslips to erode government trust and feed disinformation campaigns.
The lack of ransom demand suggests purely disruptive intent - classic state-sponsored proxy behavior.
Oracle Cloud Connection?
No evidence linking this to recent Oracle breaches. CNSS absent from Oracle customer lists, different infrastructure signatures, and internal taxonomy suggests local system compromise.
The Response (Or Lack Thereof)
CNSS finally issued a damage control statement claiming leaked documents were “misleading, inaccurate, or incomplete.” Classic bureaucratic deflection that addresses nothing.
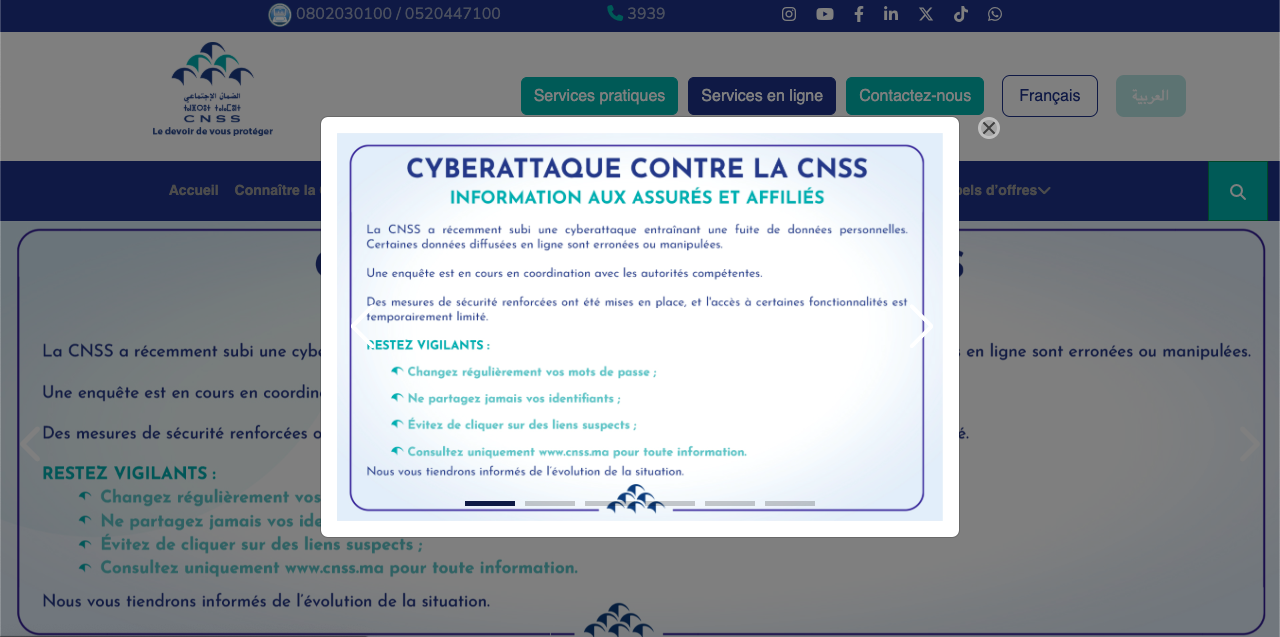
Reality check: The data is out there. BiteBlob takedowns are meaningless when the archive has already propagated through mirrors, private channels, and scraper bots.
What’s Coming:
- Targeted phishing campaigns using real employee data
- Financial fraud leveraging exposed bank details
- Identity theft operations with complete PII packages
- More breaches as other actors realize how soft these targets are
Lessons Learned
This breach wasn’t sophisticated. It exploited basic security failures:
- Outdated systems (JasperReports 6.6.0 from 2018)
- Poor access controls
- No monitoring or anomaly detection
- Weak credential management
- Legacy infrastructure with no security lifecycle
The Fix:
- Implement just-in-time access controls
- Patch or retire legacy systems
- Deploy proper monitoring and incident response
- Establish vulnerability disclosure programs
- Stop relying on security through obscurity
Security is an ecosystem you grow, not a product you buy.

Analysis based entirely on open-source intelligence. Attribution assessments are preliminary and should be treated as working hypotheses, not definitive conclusions.